System Logs: 7 Powerful Insights You Must Know in 2024
Ever wondered what your computer whispers behind the scenes? System logs hold the secrets—silent records of every action, error, and event. In this deep dive, we uncover what they are, why they matter, and how to harness their power.
What Are System Logs and Why They Matter

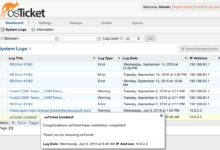
System logs are digital footprints left behind by operating systems, applications, and network devices. They chronicle everything from startup sequences to security breaches, offering a real-time window into the health and behavior of IT environments. Without them, troubleshooting would be like navigating a maze blindfolded.
The Definition and Core Purpose of System Logs
At their core, system logs are timestamped records generated by software and hardware components. Each entry typically includes a date, time, source (like a process or service), severity level, and a descriptive message. These logs serve as the first line of defense in diagnosing problems and ensuring system integrity.
- They capture operational events such as user logins, service startups, and configuration changes.
- They help identify performance bottlenecks by tracking resource usage over time.
- They act as forensic tools during security investigations.
“System logs are the black box of IT infrastructure—recording every critical moment, even when no one is watching.” — IT Operations Expert, Jane Rivera
Types of Events Captured in System Logs
Not all log entries are created equal. System logs categorize events based on their nature and impact:
- Informational: Routine operations like successful service startups or user authentications.
- Warning: Potential issues that don’t immediately disrupt service but may require attention (e.g., low disk space).
- Error: Failures in processes or services, such as a crashed application or failed login attempt.
- Critical: Severe events like system crashes, hardware failures, or security breaches.
- Debug: Detailed technical data used primarily during development or deep troubleshooting.
Understanding these categories helps administrators prioritize responses and filter noise from signal.
The Role of System Logs in IT Operations
In modern IT environments, system logs are not just helpful—they’re essential. From maintaining uptime to ensuring compliance, they form the backbone of operational visibility.
Monitoring System Health and Performance
One of the primary uses of system logs is continuous monitoring. By analyzing log data, IT teams can detect anomalies before they escalate into outages. For example, repeated disk I/O errors in the logs might indicate an impending hardware failure.
- Logs from services like
systemdon Linux or the Windows Event Log provide insights into service availability. - Performance counters logged over time help establish baselines and detect deviations.
- Tools like Nagios or Zabbix integrate with system logs to trigger alerts automatically.
According to a Gartner report, organizations that actively monitor system logs reduce unplanned downtime by up to 45%.
Supporting Incident Response and Root Cause Analysis
When something goes wrong—like a server crash or application freeze—system logs are the first place technicians look. They provide a chronological trail of events leading up to the incident.
- Correlating logs across multiple systems can reveal patterns missed in isolated views.
- Timestamps allow precise reconstruction of event sequences.
- Log entries often contain error codes or stack traces that point directly to faulty modules.
For instance, if a web server suddenly stops responding, checking the Apache or Nginx error logs might reveal a segmentation fault caused by a misconfigured module.
Security and Compliance: How System Logs Protect Your Organization
Beyond operations, system logs play a pivotal role in cybersecurity and regulatory compliance. They are often the only evidence of unauthorized access or malicious activity.
Detecting Unauthorized Access and Intrusions
Every login attempt—successful or failed—is typically recorded in system logs. A sudden spike in failed SSH attempts, for example, could signal a brute-force attack.
- On Unix-like systems, the
/var/log/auth.logfile tracks authentication events. - Windows Security Event Logs record account logins, privilege escalations, and object access.
- Intrusion Detection Systems (IDS) like Snort or OSSEC analyze system logs in real-time to flag suspicious behavior.
A well-documented case from the CISA advisory AA20-303A shows how attackers exploited weak credentials—and how system logs helped trace their lateral movement across networks.
Meeting Regulatory Requirements with Audit Trails
Many industries are legally required to maintain system logs for audit purposes. Regulations like HIPAA (healthcare), PCI-DSS (payment processing), and GDPR (data privacy) mandate log retention and protection.
- HIPAA requires logging of all access to electronic protected health information (ePHI).
- PCI-DSS mandates daily review of system logs for all critical systems handling cardholder data.
- GDPR doesn’t specify logging directly but requires organizations to demonstrate accountability and data protection—logs help prove compliance.
Failure to maintain proper system logs can result in hefty fines. In 2022, a European company was fined €2.1 million under GDPR partly due to inadequate logging and monitoring practices.
Common Sources and Formats of System Logs
System logs come from a wide variety of sources, each with its own format and structure. Understanding these differences is key to effective log management.
Operating System-Level Logs
Every operating system generates its own set of system logs. These are foundational to any IT environment.
- Linux: Uses
syslogorjournald(viasystemd) to manage logs. Key files include/var/log/messages,/var/log/syslog, and/var/log/kern.log. - Windows: Relies on the Windows Event Log service, which organizes events into channels like Application, Security, and System.
- macOS: Combines
syslogwith the Unified Logging System introduced in macOS Sierra, storing logs in a binary format accessible via thelogcommand.
These logs are often the first place administrators check when diagnosing issues.
Application and Service Logs
Beyond the OS, individual applications generate their own system logs. Web servers, databases, and email services all maintain detailed records.
- Apache HTTP Server logs access and errors to
access.loganderror.log. - MySQL and PostgreSQL write query errors, slow queries, and connection attempts to dedicated log files.
- Email servers like Postfix or Exchange generate logs for message routing, delivery failures, and spam filtering.
These application-specific logs are crucial for debugging software issues and optimizing performance.
Network Device Logs
Routers, switches, firewalls, and load balancers also produce system logs, typically using the Syslog protocol.
- Firewalls like Cisco ASA or Palo Alto log blocked connections, policy violations, and threat detections.
- Switches log port status changes, STP events, and VLAN modifications.
- Load balancers record health checks, session persistence, and SSL handshake failures.
Centralizing these logs allows network teams to monitor traffic patterns and detect anomalies at scale.
Best Practices for Managing System Logs
Collecting logs is just the beginning. To derive real value, organizations must manage them effectively—ensuring they are secure, searchable, and retained appropriately.
Centralized Logging and Log Aggregation
In distributed environments, logs are scattered across dozens or hundreds of machines. Centralized logging solves this by collecting all system logs into a single repository.
- Tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Graylog aggregate logs from diverse sources.
- Agents like Filebeat or Fluentd ship logs from endpoints to central servers securely.
- Cloud platforms like AWS CloudWatch or Azure Monitor offer native log aggregation services.
Centralization enables faster searching, better correlation, and improved compliance reporting.
Log Rotation and Retention Policies
Logs can consume massive amounts of disk space over time. Without rotation, they can fill up storage and crash systems.
- Log rotation involves compressing old logs and deleting them after a set period.
- On Linux,
logrotateis commonly used to automate this process. - Retention policies should align with legal and business requirements—e.g., 90 days for operational logs, 1 year for security logs.
A 2023 survey by Splunk found that 68% of companies without formal log retention policies experienced compliance audit failures.
Securing System Logs Against Tampering
Logs are only trustworthy if they haven’t been altered. Attackers often delete or modify system logs to cover their tracks.
- Store logs on write-once, read-many (WORM) storage or immutable cloud buckets.
- Use cryptographic hashing to detect tampering.
- Send logs to a remote, hardened server that users cannot access directly.
The NIST SP 800-92 guide emphasizes log integrity as a cornerstone of effective security monitoring.
Tools and Technologies for Analyzing System Logs
Raw logs are overwhelming. Specialized tools transform them into actionable insights through parsing, visualization, and alerting.
Open Source Log Management Solutions
For organizations seeking cost-effective options, open-source tools offer powerful log analysis capabilities.
- ELK Stack: Elasticsearch indexes logs, Logstash processes them, and Kibana provides dashboards.
- Graylog: Offers centralized logging with alerting, extraction, and role-based access control.
- Rsyslog: A high-performance syslog server capable of handling millions of messages per second.
These tools are highly customizable and widely supported by active communities.
Commercial and Cloud-Based Platforms
Enterprises often prefer commercial solutions for scalability, support, and integration.
- Datadog: Combines log management with metrics and APM in a unified platform.
- Splunk: One of the most powerful log analysis tools, used extensively in security and IT operations.
- AWS CloudWatch Logs: Native to Amazon Web Services, it integrates seamlessly with EC2, Lambda, and other services.
According to IDC, spending on cloud-based log management tools grew by 22% year-over-year in 2023.
Real-Time Monitoring and Alerting Systems
Waiting for a system to fail isn’t an option. Real-time log analysis enables proactive incident response.
- Tools like Prometheus with Alertmanager can parse logs and trigger alerts based on thresholds.
- Splunk’s correlation searches detect multi-stage attacks by analyzing sequences of log events.
- PagerDuty integrates with logging platforms to notify teams via SMS, email, or phone calls.
For example, a sudden surge in 500 errors in web server logs can automatically trigger an alert to the DevOps team before users are affected.
Challenges and Pitfalls in System Log Management
Despite their value, managing system logs comes with significant challenges—from volume overload to misconfigurations.
Dealing with Log Volume and Noise
Modern systems generate terabytes of logs daily. Sifting through irrelevant entries—like routine informational messages—can drown out critical alerts.
- Implement log filtering to suppress low-severity messages in production.
- Use AI-powered tools to detect anomalies and reduce false positives.
- Apply structured logging (e.g., JSON format) to make parsing easier.
A study by IBM found that security analysts spend nearly 30% of their time investigating false alerts—many stemming from poorly filtered system logs.
Ensuring Log Integrity and Availability
If logs are lost or corrupted, their value disappears. Ensuring availability and integrity is a constant challenge.
- Back up logs regularly to offsite or cloud storage.
- Use redundant logging paths (e.g., local + remote) to prevent single points of failure.
- Monitor log collection agents to ensure they’re running and not dropping messages.
During a ransomware attack in 2021, a healthcare provider lost critical system logs because the logging server was on the same network segment as infected machines.
Common Configuration Mistakes
Even small misconfigurations can render system logs useless.
- Incorrect log levels (e.g., setting everything to DEBUG) flood systems with noise.
- Improper time synchronization (NTP misconfigurations) breaks event correlation.
- Failure to secure log files allows unauthorized access or deletion.
One common mistake: storing logs on the same disk as the OS. If the system crashes or runs out of space, logs may be lost just when they’re needed most.
Future Trends in System Logs and Log Analytics
As technology evolves, so do system logs. Emerging trends are reshaping how we collect, analyze, and act on log data.
The Rise of AI and Machine Learning in Log Analysis
Traditional rule-based alerting is giving way to intelligent systems that learn normal behavior and detect deviations.
- AI models can identify subtle attack patterns missed by human analysts.
- Unsupervised learning clusters similar log events to reduce noise.
- Natural Language Processing (NLP) helps extract meaning from unstructured log messages.
Google’s Chronicle uses AI to analyze petabytes of system logs, identifying threats in seconds rather than hours.
Integration with Observability and DevOps Practices
Logs are now part of a broader observability strategy that includes metrics, traces, and user feedback.
- Modern DevOps teams use tools like OpenTelemetry to correlate logs with distributed traces.
- Site Reliability Engineers (SREs) rely on logs to measure service level objectives (SLOs).
- GitOps workflows automatically update logging configurations via version-controlled manifests.
Observability isn’t just about seeing what’s broken—it’s about understanding why it broke.
Cloud-Native and Containerized Logging Challenges
With the rise of Kubernetes and microservices, logs are more ephemeral than ever.
- Containers start and stop rapidly, making log persistence a challenge.
- Sidecar logging patterns (e.g., Fluentd in a pod) help capture logs before containers vanish.
- Service meshes like Istio generate rich logs for inter-service communication.
According to the 2023 Cloud Native Survey, 74% of organizations struggle with log aggregation in containerized environments.
What are system logs used for?
System logs are used for monitoring system health, diagnosing technical issues, detecting security threats, ensuring compliance with regulations, and conducting forensic investigations after incidents.
Where are system logs stored on Linux and Windows?
On Linux, system logs are typically stored in /var/log/ (e.g., /var/log/syslog, /var/log/auth.log). On Windows, they are managed by the Event Viewer and stored in binary files within C:WindowsSystem32winevtLogs.
How long should system logs be retained?
Retention periods vary by industry and regulation. General best practices suggest keeping security logs for at least 90 days, though PCI-DSS requires one year. Some organizations retain logs for up to 7 years for legal or compliance reasons.
Can system logs be faked or deleted by attackers?
Yes, attackers often delete or alter system logs to hide their activities. This is why securing logs—by sending them to immutable, remote storage—is critical for maintaining forensic integrity.
What is the best tool for analyzing system logs?
There is no single “best” tool—it depends on your needs. For open-source solutions, ELK Stack and Graylog are popular. For enterprise use, Splunk and Datadog offer advanced features. Cloud users often prefer AWS CloudWatch or Azure Monitor.
System logs are far more than technical artifacts—they are the heartbeat of modern IT infrastructure. From troubleshooting everyday glitches to defending against cyberattacks, they provide the visibility needed to keep systems running smoothly. As technology advances, so too must our approach to logging: embracing automation, AI, and cloud-native practices. By mastering system logs today, organizations can build more resilient, secure, and efficient digital environments for tomorrow.
Further Reading: